Cybersecurity SIEM-plified
We understand you may not be a security expert. That’s okay. We have a team of security experts who make technology simple. SIEM, or security information and event management, is a powerful tool for businesses that want to protect their systems, data, and reputation from security threats and cyber-attacks.
What is SIEM?
It can take several days, even months, to identify a data compromise, and it’s easy to see why. Modern security tools can generate millions of security alerts over the course of a day. That’s where SIEM comes in.
A SIEM solution filters out the noise, so the real threats get immediate attention. It provides real-time threat detection, incident response, compliance, and operational efficiency, helping businesses stay one step ahead of potential security breaches and minimize the impact of security incidents.

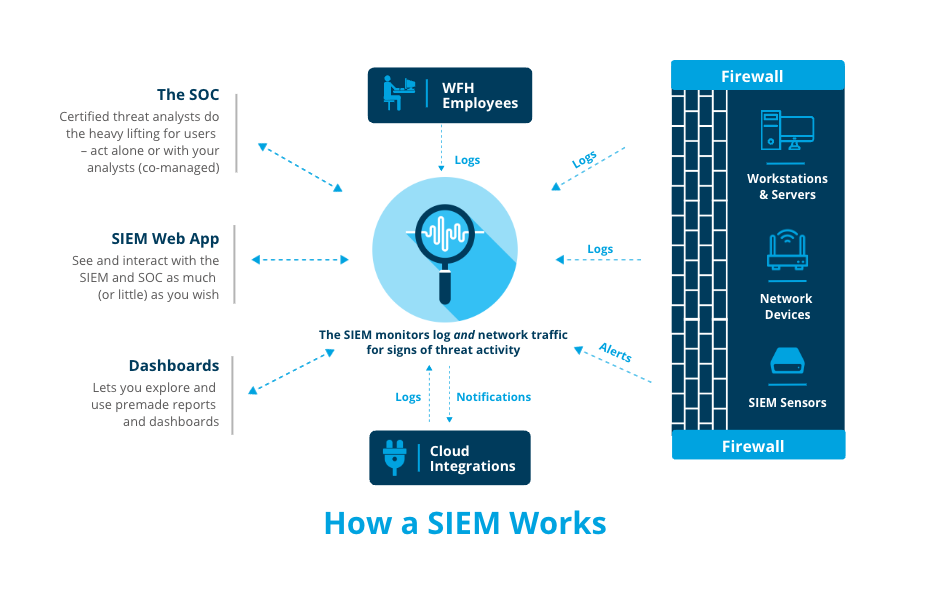
How does SIEM work?
SIEM collects and analyzes security event logs from different sources within your IT infrastructure, including network devices, servers, applications, and endpoints, to provide a centralized view of security events and incidents. It uses advanced analysis and cross-correlation to automatically filter out false alerts so real threats bubble to the surface.
Why do you need a SIEM?
Many organizations are faced with limited IT resources and cybersecurity expertise, which can be costly and cause complex issues. Download our infosheet 5 Reasons Your Business Needs a SIEM to learn more.

Benefits of SIEM
When utilizing a SIEM, your business can expect to benefit from:
Full network visibility
Real-time expertise
24×7 security operations center (SOC)
Compliance requirements
Enhanced threat visibility
Reduced costs with solution management
Resources

We get it – the cybersecurity world is inundated with complex anacronyms that are often difficult to decipher….
Read MoreSchedule a Security Assessment
Fill out the contact form to schedule a security assessment and SIEM demo.

